Application development team users are having issues accessing the database server within the cloud environment. All other users are able to use SSH to access this server without issues. The network architect reviews the following information to troubleshoot the issue:
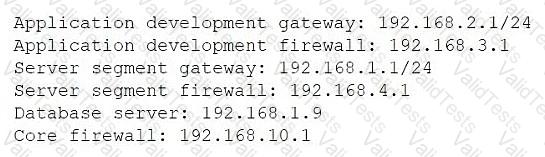
Traceroute output from an application developer's machine with the assigned IP 192.168.2.7:
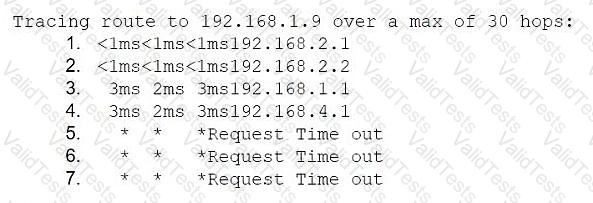
Application development gateway: 192.168.2.1/24
Server segment gateway: 192.168.1.1/24
Database server: 192.168.1.9
Application developer machine IP: 192.168.2.7
Traceroute ends at hop 4: 192.168.4.1 (server segment firewall), then times out
Which of the following is the most likely cause of the issue?
A network administrator must connect a remote building at a manufacturing plant to the main building via a wireless connection. Which of the following should the administrator choose to get the greatest possible range from the wireless connection? (Choose two.)
A company's IT department is expected to grow from 100 to 200 employees, and the sales department is expected to grow from 1,000 to a maximum of 2,000 employees. Each employee owns a single laptop with a single IP allocated. The network architect wants to deploy network segmentation using the IP range 10.0.0.0/8. Which of the following is the best solution?
Server A (10.2.3.9) needs to access Server B (10.2.2.7) within the cloud environment since theyare segmented into different network sections. All external inbound traffic must be blocked to those servers. Which of the following need to be configured to appropriately secure the cloud network? (Choose two.)
A network engineer at an e-commerce organization must improve the following dashboard due to a performance issue on the website:
(Refer to the image: Website performance monitoring dashboard showing metrics like network usage, CPU usage, memory usage, and disk usage over time.)
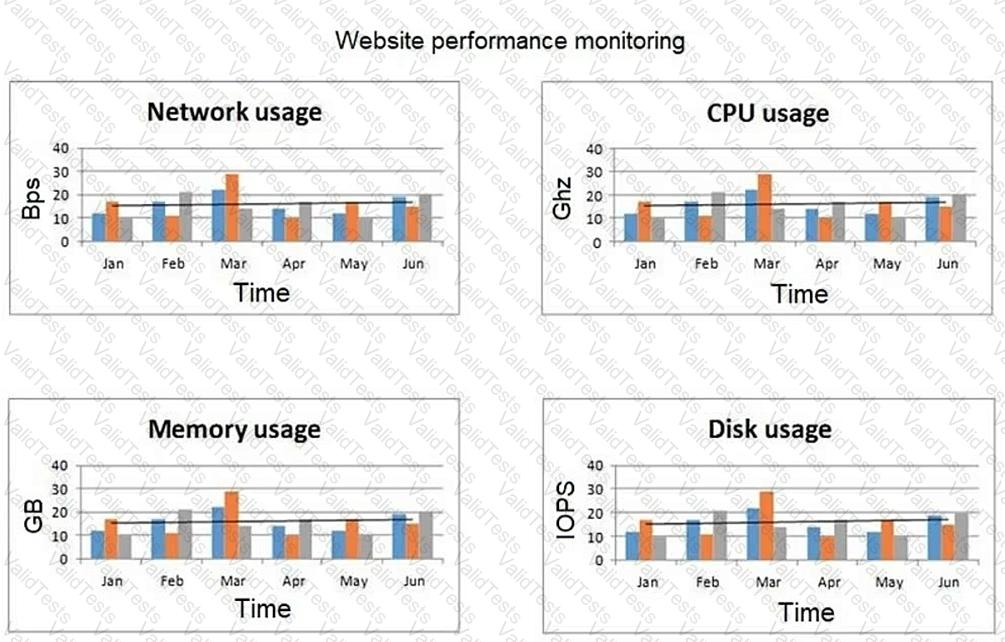
Which of the following is the most useful information to add to the dashboard for the operations team?
A network architect is designing an expansion solution for the branch office network and requires the following business outcomes:
Maximize cost savings with reduced administration overhead
Easily expand connectivity to the cloud
Use cloud-based services to the branch offices
Which of the following should the architect do to best meet the requirements?
A developer reports errors when trying to access a web application. The developer uses Postman to troubleshoot and receives the following error:
HTTP Status: 403 Forbidden
Headers include authentication-related variables such as access_key, signature, salt, and timestamp
The request is a GET request to a payment methods API
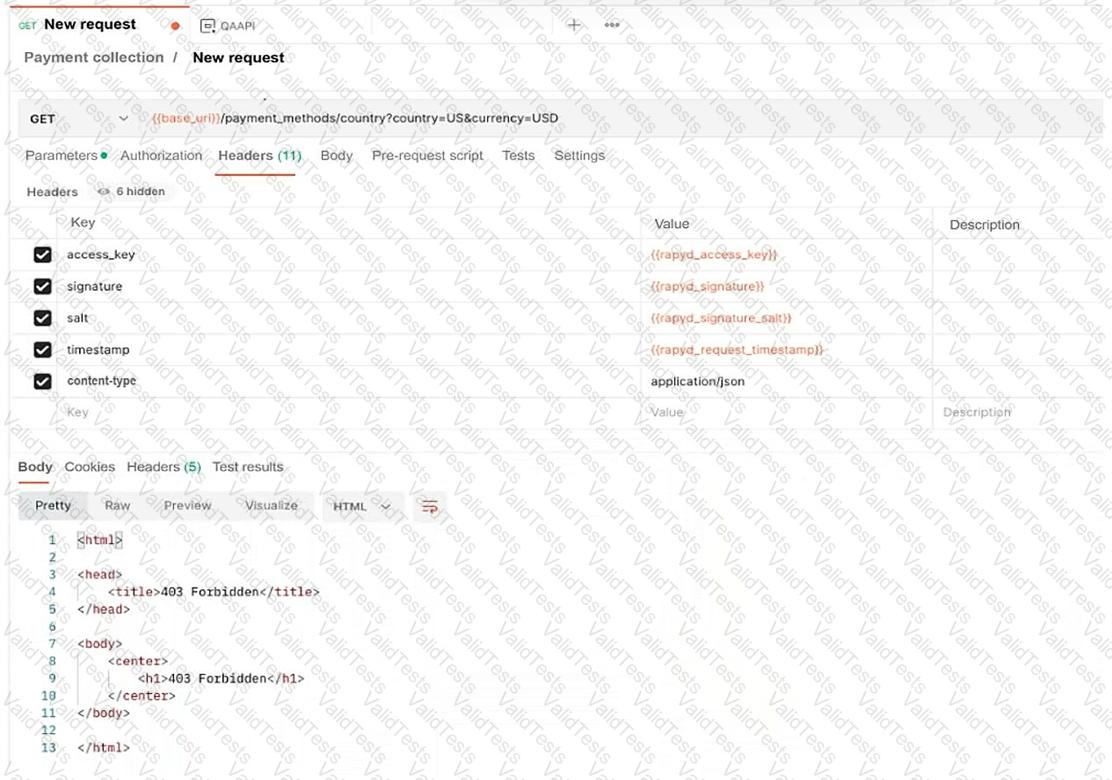
Which of the following is the cause of the issue?
An organization's Chief Technical Officer is concerned that changes to the network using IaC are causing unscheduled outages. Which of the following best mitigates this risk?
A network security engineer must secure a web application running on virtual machines in a public cloud. The virtual machines are behind an application load balancer. Which of the following technologies should the engineer use to secure the virtual machines? (Choose two.)
After a malicious actor used an open port in a company's lobby, a network architect needs to enhance network security. The solution must enable:
Security posture check
Auto remediation capabilities
Network isolation
Device and user authentication
Which of the following technologies best meets these requirements?