An external consulting firm is hired to perform a penetration test and must keep the confidentiality of the security vulnerabilities and the private data found in a customer's systems. Which of the following documents addresses this requirement?
During a penetration testing engagement, a penetration tester discovers a buffer overflow vulnerability. Which of the following actions should the tester take to maintain professionalism and integrity?
Which of the following best explains why a penetration tester would use ProxyChains during an assessment?
An organization's Chief Information Security Officer debates the validity of a critical finding from a penetration assessment that was completed six months ago. Which of the following post-report delivery activities would have most likely prevented this scenario?
A client claims that a ransomware attack has crippled its corporate network following a penetration test assessment. Which of the following is the most likely root cause of this issue?
A penetration tester runs a reconnaissance script and would like the output in a standardized machine-readable format in order to pass the data to another application. Which of the following is the best for the tester to use?
A penetration tester discovered a vulnerability that has the following CVEs:
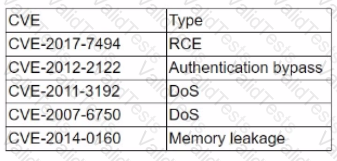
Which of the following CVEs should be remediated first?
Which of the following should be included in scope documentation?
During a security assessment of a web application, a penetration tester was able to generate the following application response:
Unclosed quotation mark after the character string Incorrect syntax near ".
Which of the following is the most probable finding?
During an assessment, a penetration tester discovers the following code sample in a web application:
"(&(userid=*)(userid=*))(I(userid=*)(userPwd=(SHAl}a9993e364706816aba3e25717850c26c9cd0d89d==))
Which of the following injections is being performed?