What feature is designed to exclude applications from CyberArk EPM's Ransomware Protection, without whitelisting the application launch?
In EPM, creation of which user type is required to use SAML?
An application has been identified by the LSASS Credentials Harvesting Module.
What is the recommended approach to excluding the application?
When adding the EPM agent to a pre-existing security stack on workstation, what two steps are CyberArk recommendations. (Choose two.)
When deploying EPM and in the Privilege Management phase what is the purpose of Discovery?
Which EPM reporting tool provides a comprehensive view of threat detection activity?
A policy needs to be created to block particular applications for a specific user group. Based on CyberArk's policy naming best practices, what should be included in the policy's name?
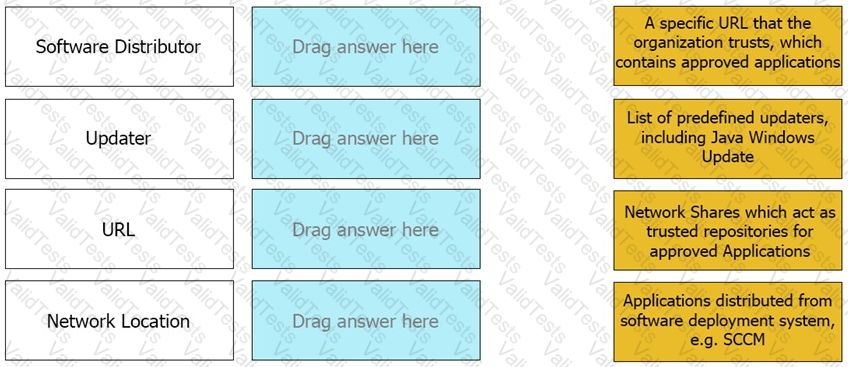
Match the Trusted Source to its correct definition:
When enabling Threat Protection policies, what should an EPM Administrator consider? (Choose two.)
An EPM Administrator would like to notify end users whenever the Elevate policy is granting users elevation for their applications. Where should the EPM Administrator go to enable the end-user dialog?