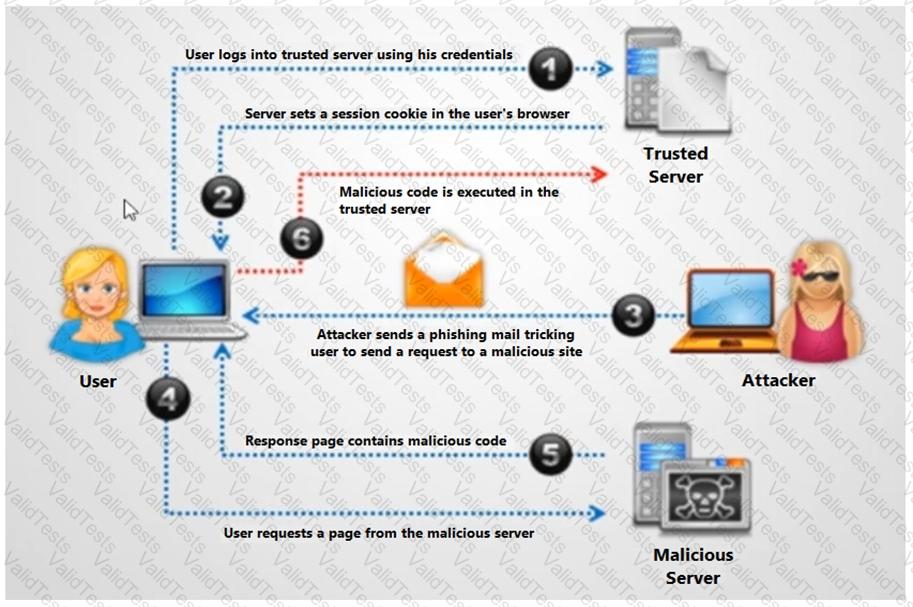
Identify the type of attack depicted in the figure below:
According to secure logging practices, programmers should ensure that logging processes are not disrupted by:
Which of the following method will help you check if DEBUG level is enabled?
Oliver is a web server admin and wants to configure the Tomcat server in such a way that it should not serve index pages in the absence of welcome files. Which of the following settings in CATALINA_HOME/conf/ in web.xml will solve his problem?
A US-based ecommerce company has developed their website www.ec-sell.com to sell their products online. The website has a feature that allows their customer to search products based on the price. Recently, a bug bounty has discovered a security flaw in the Search page of the website, where he could see all products from the database table when he altered the website URL http://www.ec-sell.com/products.jsp?val=100 to http://www.ec-sell.com/products.jsp?val=200 OR '1'='1 -. The product.jsp page is vulnerable to
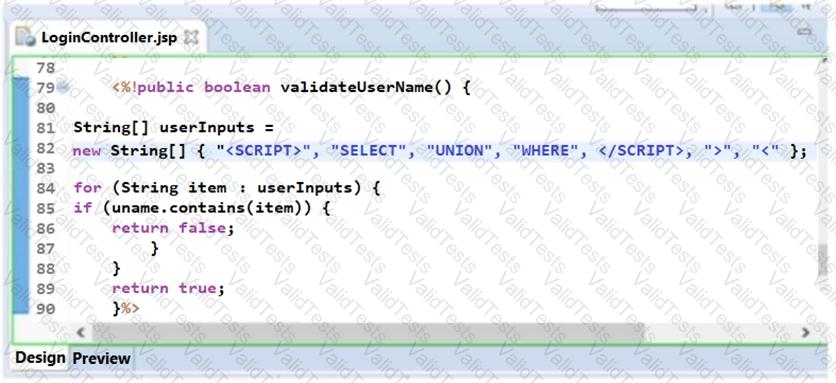
Sam, an application security engineer working in INFRA INC., was conducting a secure code review on an application developed in Java. He found that the developer has used a piece of code as shown in the following screenshot. Identify the security mistakes that the developer has coded?
Which of the following configuration settings in server.xml will allow Tomcat server administrator to impose limit on uploading file based on their size?
Identify what should NOT be catched while handling exceptions.
The developer wants to remove the HttpSessionobject and its values from the client' system.
Which of the following method should he use for the above purpose?
Which of the following state management method works only for a sequence of dynamically generated forms?