
View all detail and faqs for the FCSS_SASE_AD-23 exam
When deploying FortiSASE agent-based clients, which three features are available compared to an agentless solution? (Choose three.)
What are two advantages of using zero-trust tags? (Choose two.)
Refer to the exhibit.

To allow access, which web tiller configuration must you change on FortiSASE?
How does FortiSASE hide user information when viewing and analyzing logs?
Refer to the exhibit.
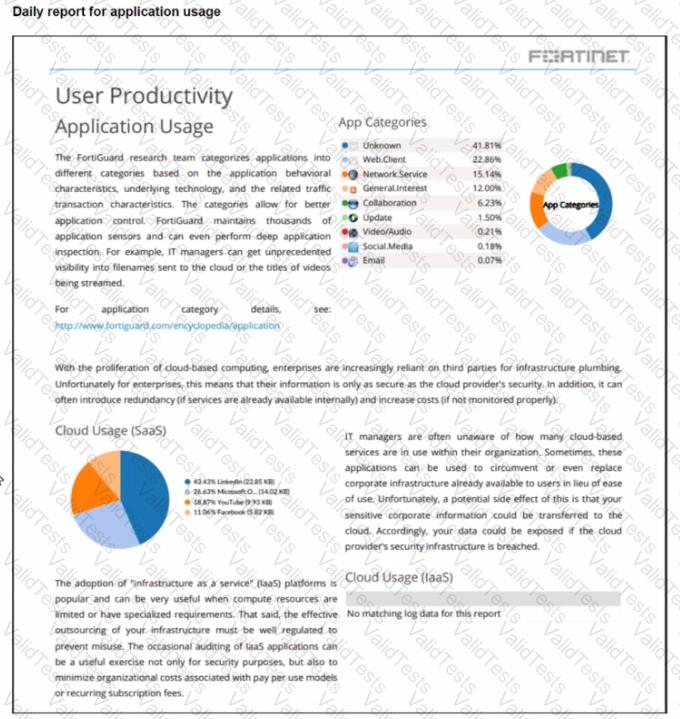
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
Which two deployment methods are used to connect a FortiExtender as a FortiSASE LAN extension? (Choose two.)
Refer to the exhibits.

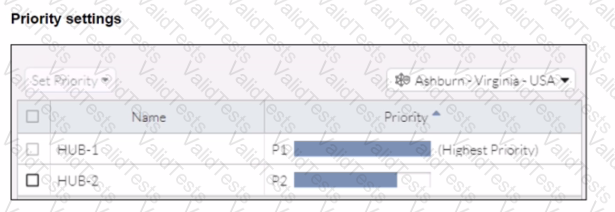
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
Refer to the exhibit.
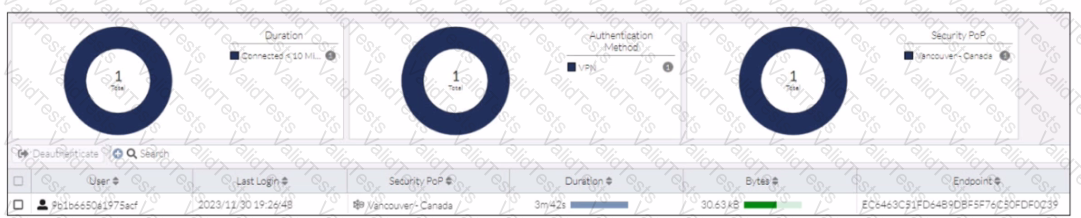
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
Which policy type is used to control traffic between the FortiClient endpoint to FortiSASE for secure internet access?