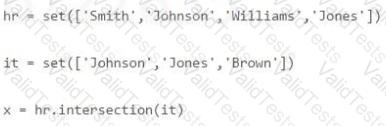
What will the following code in Python 3 result in?

A log file is stored in variable "a". The file has the following format for each log entry, in order, stored in big endian:
Field 1: 2-byte integer
Field 2: 2-byte integer
Field 3: 4-byte string
Which of the following would unpack a line from the log file into the proper fields?
What does the attacker do in a SQL Injection attack?
After calling a subprocess in a Python program, the program returns an error code of "0". What does this indicate?
What is the output of the Is(TCP) function?
Which of the following would produce this list?
[65, 66, 67, 68]
An attacker does not yet know the IP address of his target. He uses the "socket" module to create a backdoor program. He is writing the command to bind the computer's current IP address and port 4444 to the "backdoor" socket. Which command should he use?
What wilt the code in the screen capture print when executed?

Which of the following commands would correct the error in the screenshot?
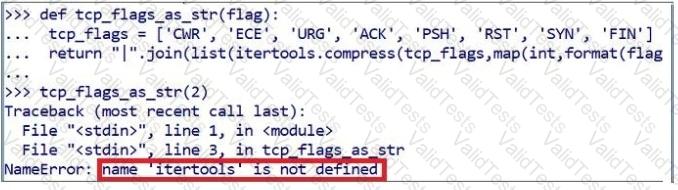
Review the following Python code: