
View all detail and faqs for the NetSec-Generalist exam
Which two policies in Strata Cloud Manager (SCM) will ensure the personal data of employees remains private while enabling decryption for mobile users in Prisma Access? (Choose two.)
Which two SSH Proxy decryption profile configurations will reduce network attack surface? (Choose two.)
After a Best Practice Assessment (BPA) is complete, it is determined that dynamic updates for Cloud-Delivered Security Services (CDSS) used by company branch offices do not match recommendations. The snippet used for dynamic updates is currently set to download and install updates weekly.
Knowing these devices have the Precision Al bundle, which two statements describe how the settings need to be adjusted in the snippet? (Choose two.)
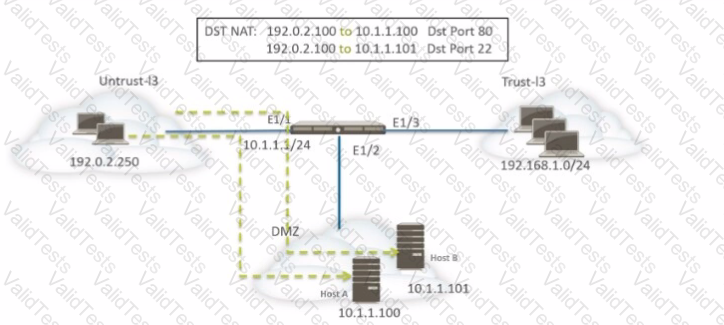
A network administrator is using DNAT to map two servers to one public IP address. Traffic will be directed to a specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic.
Which two sets of Security policy rules will accomplish this configuration? (Choose two.)
Why would an enterprise architect use a Zero Trust Network Access (ZTNA) connector instead of a service connection for private application access?
In Prisma SD-WAN. what is the recommended initial action when VoIP traffic experiences high latency and packet loss during business hours?
Which two security profiles must be updated to prevent data exfiltration in outbound traffic on NGFWs? (Choose two.)
A network engineer needs to configure a Prisma SD-WAN environment to optimize and secure traffic flow between branch offices and the data center.
Which action should the engineer prioritize to achieve the most operationally efficient communication?
A company uses Prisma Access to provide secure connectivity for mobile users to access its corporate-sanctioned Google Workspace and wants to block access to all unsanctioned Google Workspace environments.
What would an administrator configure in the snippet to achieve this goal?
A network security engineer wants to forward Strata Logging Service data to tools used by the Security Operations Center (SOC) for further investigation.
In which best practice step of Palo Alto Networks Zero Trust does this fit?