Which two actions will allow a security analyst to review updated commands from the core pack and interpret the results without altering the incident audit? (Choose two)
For a critical incident, Cortex XSIAM suggests several playbooks which should have been executed automatically.
Why were the playbooks not executed?
An incident in Cortex XSIAM contains the following series of alerts:
10:24:17 AM - Informational Severity - XDR Analytics BIOC - Rare process execution in organization
10:24:18 AM - Low Severity - XDR BIOC - Suspicious AMSI DLL load location
10:24:20 AM - Medium Severity - XDR Agent - WildFire Malware
11:57:04 AM - High Severity - Correlation - Suspicious admin account creation
Which alert was responsible for the creation of the incident?
Which two actions can an analyst take to reduce the number of false positive alerts generated by a custom BIOC? (Choose two.)
Which statement applies to a low-severity alert when a playbook trigger has been configured?
Which two statements apply to IOC rules? (Choose two)
An analyst is responding to a critical incident involving a potential ransomware attack. The analyst immediately initiates full isolation on the compromised endpoint using Cortex XSIAM to prevent the malware from spreading across the network. However, the analyst now needs to collect additional forensic evidence from the isolated machine, including memory dumps and disk images without reconnecting it to the network. Which action will allow the analyst to collect the required forensic evidence while ensuring the endpoint remains fully isolated?
When a sub-playbook loops, which task tab will allow an analyst to determine what data the sub-playbook used in each iteration of the loop?
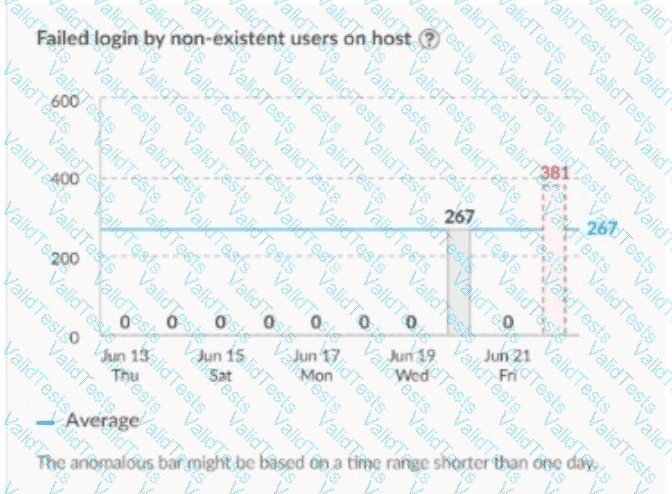
Which type of analytics will trigger the alert on the image shown?
Which two methods can be used to create and share queries into the Query Library? (Choose two.)