As data enters the indexer, it proceeds through a pipeline where event processing occurs. In which pipeline does line breaking occur?
Which statement is correct?
The customer has an indexer cluster supporting a wide variety of search needs, including scheduled search, data model acceleration, and summary indexing. Here is an excerpt from the cluster mater’s server.conf:

Which strategy represents the minimum and least disruptive change necessary to protect the searchability of the indexer cluster in case of indexer failure?
Which configuration item should be set to false to significantly improve data ingestion performance?
A customer has a network device that transmits logs directly with UDP or TCP over SSL. Using PS best practices, which ingestion method should be used?
Which event processing pipeline contains the regex replacement processor that would be called upon to run event masking routines on events as they are ingested?
A new search head cluster is being implemented. Which is the correct command to initialize the deployer node without restarting the search head cluster peers?
What is the default push mode for a search head cluster deployer app configuration bundle?
A customer has written the following search:
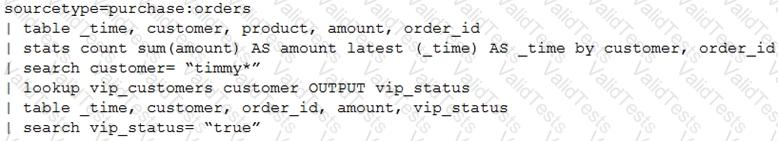
How can the search be rewritten to maximize efficiency?
Consider the scenario where the /var/log directory contains the files secure, messages, cron, audit. A customer has created the following inputs.conf stanzas in the same Splunk app in order to attempt to monitor the files secure and messages:
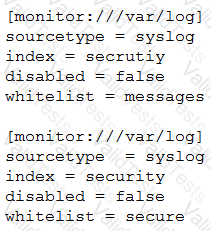
Which file(s) will actually be actively monitored?