You are collecting data after a suspected intrusion on the local LAN.
You need to capture incoming IP packets to a file for an investigator to analyze.
Which two tools should you use?(Choose 2.)
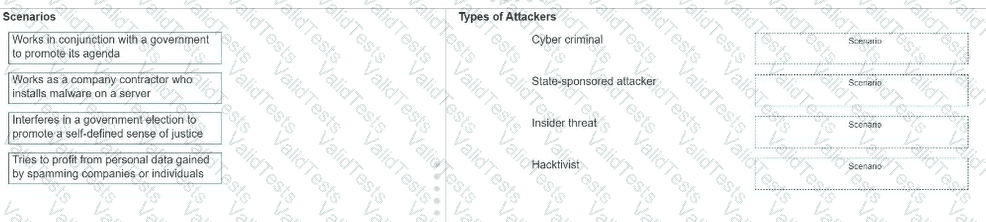
Move each scenario from the list on the left to the correct type of attacker on the right.
Note: You will receive partial credit for each correct answer.
What should you create to prevent spoofing of the internal network?
How does sandboxing help with the analysis of malware?
During an incident response, the security team needs to isolate a compromised server from the rest of the network but still allow forensic analysis. Which action should they take?
You notice that a new CVE has been shared to an email group that you belong to.
What should you do first with the CVE?
A threat actor sets up a rogue access point (AP) at a local cafe. The rogue AP captures traffic and then forwards the traffic to the cafe AP.
Which type of attack does this scenario describe?
You need to design your company’s password policy to adhere to the National Institute of Standards and Technology (NIST) guidelines for user password security.
What is the minimum password length that you should require to be consistent with the NIST guidelines?
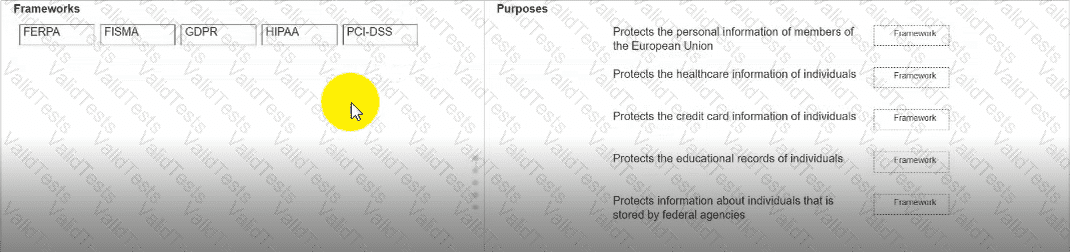
Move each framework from the list on the left to the correct purpose on the right.
Note: You will receive partial credit for each correct answer.
A restaurant installs a second wireless router that only employees can use.
Which statement describes how to securely configure the new router?