A security team detected an above-average amount of inbound tcp/135 connection attempts from unidentified senders. The security team is responding based on their incident response playbook. Which two elements are part of the eradication phase for this incident? (Choose two.)
Which type of record enables forensics analysts to identify fileless malware on Windows machines?
Refer to the exhibit.
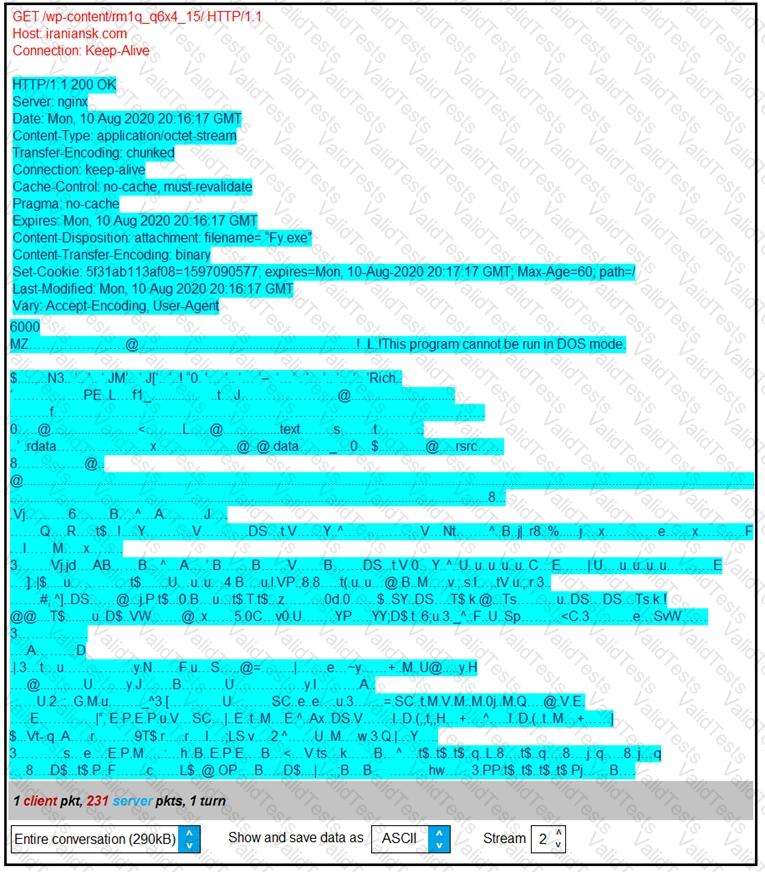
According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
In a secure government communication network, an automated alert indicates the presence of anomalous DLL files injected into the system memory during a routine update of communication protocols. These DLL files are exhibiting beaconing behavior to a satellite IP known for signal interception risks. Concurrently, there is an uptick in encrypted traffic volumes that suggests possible data exfiltration. Which set of actions should the security engineer prioritize?
Refer to the exhibit.
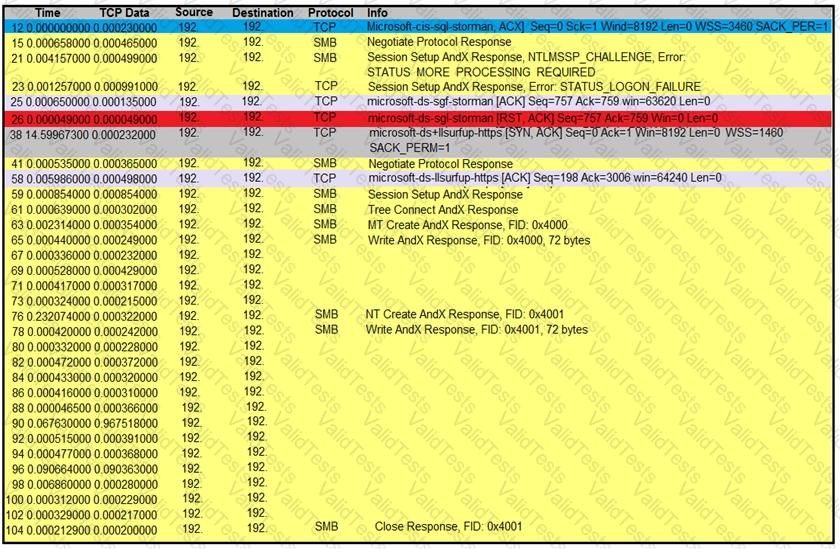
An engineer is analyzing a TCP stream in Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
Which tool should be used for dynamic malware analysis?
Refer to the exhibit.
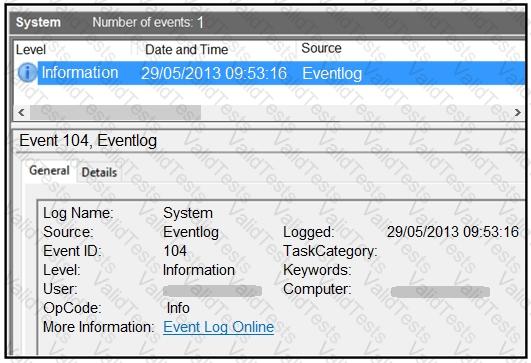
An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
Refer to the exhibit.
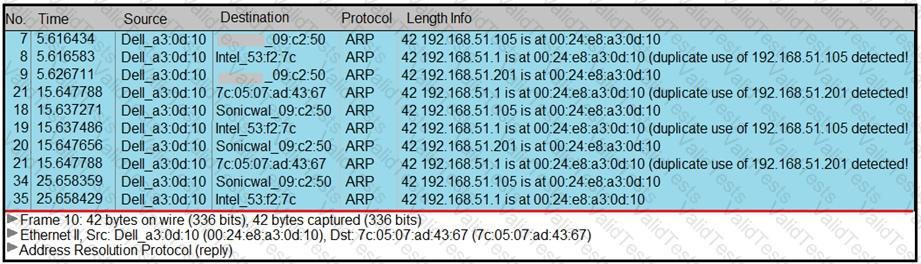
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
Refer to the exhibit.

What is occurring?