An administrator has deployed an NC2 on AWS cluster that is running mixed workloads. Multiple SQL database are running on the NC2 cluster using a native subnet of 10.78.1.0/24.
The administrator wants to ensure only application servers from source subnet 10.79.1.0/24 that reside outside of the NC2 cluster can access the databases.
Which two actions will help the administrator most securely achieve this? (Choose two.)
A)
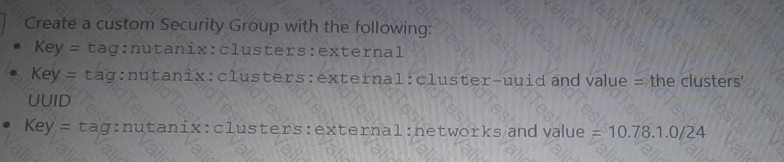
B)

C)

D)
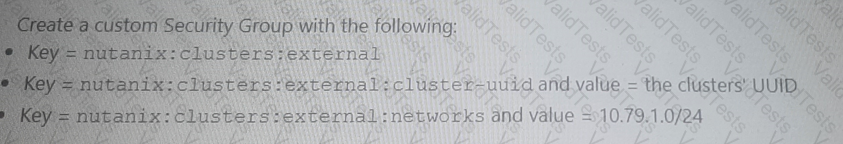
Submit