To which phase of the Computer Forensics Investigation Process does the Planning and Budgeting of a Forensics Lab belong?
Which program is the bootloader when Windows XP starts up?
Which of the following is a database in which information about every file and directory on an NT File System (NTFS) volume is stored?
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away.
Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
Paraben Lockdown device uses which operating system to write hard drive data?
When using an iPod and the host computer is running Windows, what file system will be used?
Jacob is a computer forensics investigator with over 10 years experience in investigations and has written over 50 articles on computer forensics. He has been called upon as a qualified witness to testify the accuracy and integrity of the technical log files gathered in an investigation into computer fraud. What is the term used for Jacob testimony in this case?
Amber, a black hat hacker, has embedded a malware into a small enticing advertisement and posted it on a popular ad-network that displays across various websites. What is she doing?
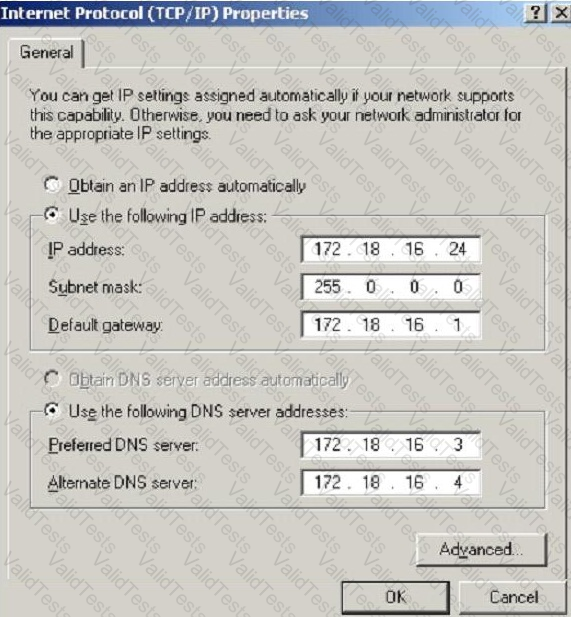
What is the CIDR from the following screenshot?
How will you categorize a cybercrime that took place within a CSP’s cloud environment?
Charles has accidentally deleted an important file while working on his Mac computer. He wants to recover the deleted file as it contains some of his crucial business secrets. Which of the following tool will help Charles?
Watson, a forensic investigator, is examining a copy of an ISO file stored in CDFS format. What type of evidence is this?
Bob has encountered a system crash and has lost vital data stored on the hard drive of his Windows computer. He has no cloud storage or backup hard drives. he wants to recover all those data, which includes his personal photos, music, documents, videos, official email, etc. Which of the following tools shall resolve Bob’s purpose?
What is one method of bypassing a system BIOS password?
Smith, a forensic examiner, was analyzing a hard disk image to find and acquire deleted sensitive files. He stumbled upon a $Recycle.Bin folder in the root directory of the disk. Identify the operating system in use.