An administrator has just learned that an intermediate CA certificate signed by a FortiAuthenticator device acting as the Root CA has been compromised.
Which two steps should the administrator take to resolve the security issue? (Choose two.)
Which option correctly describes an SP-initiated SSO SAML packet flow for a host without a SAML assertion?
You are a FortiAuthenticator administrator for a large organization. Users who are configured to use FortiToken 200 for two-factor authentication can no longer authenticate. You have verified that only the users with two-factor authentication are experiencing the issue.
What can cause this issue?
A network administrator is using FortiAuthenticator as their RADIUS server for wired and wireless network access. The administrator wants to pass the users' group information back to the RADIUS clients when the users authenticate.
How does FortiAuthenticator accomplish this?
When creating an administrative user, what capabilities does the Web service access option provide?
Which two statements about asymmetric cryptography are true? (Choose two.)
Refer to the exhibit.
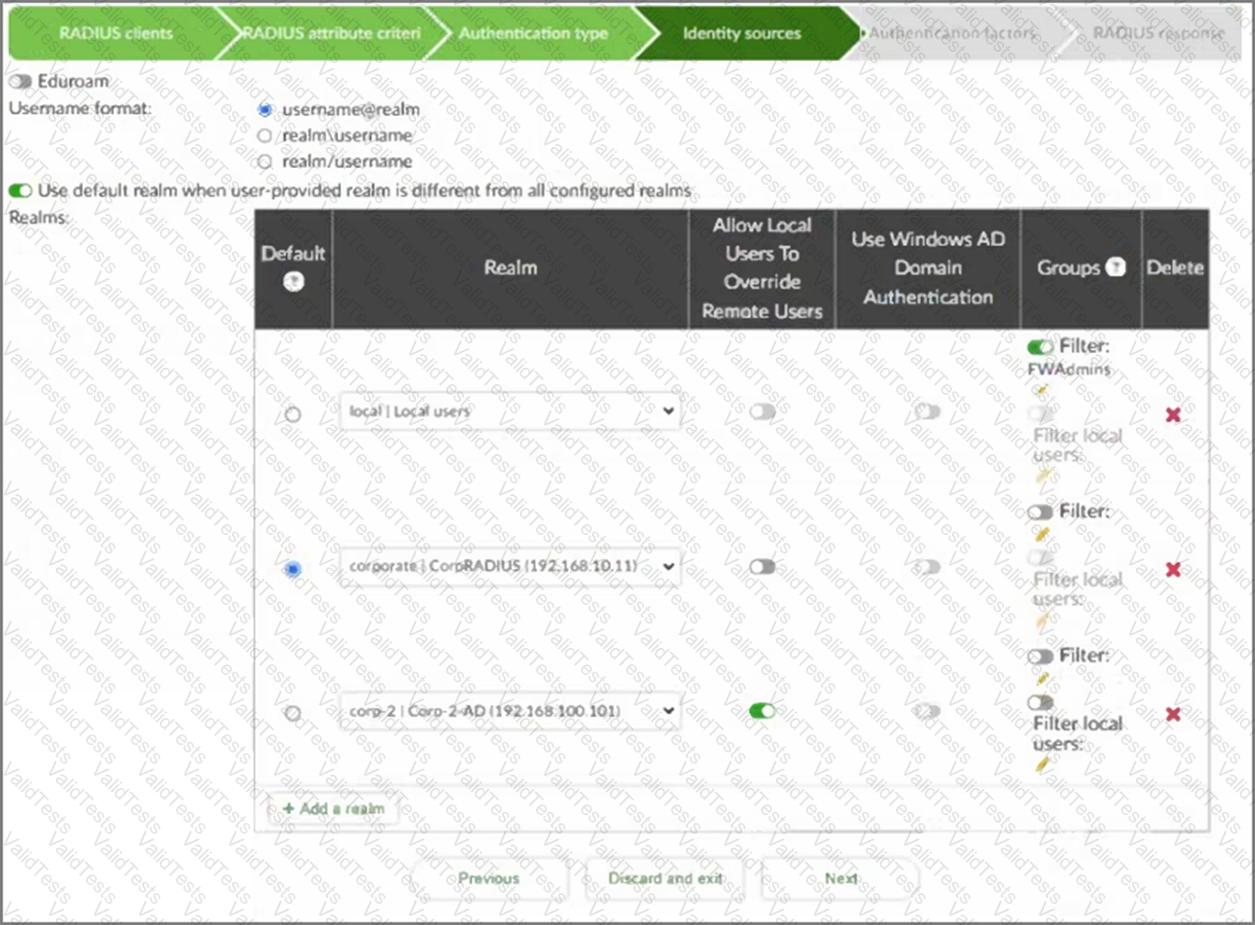
Examine the RADIUS policy configuration shown in the exhibit. A user attempts to authenticate by entering the usernamejdoe@example.comand their password.
Which realm will the user be authenticated against?
Which FSSO discovery method transparently detects logged off users without having to rely on external features such as WMI polling?
When performing a remote LDAP server integration with FortiAuthenticator, how do server type templates assist with the integration?