
View all detail and faqs for the FCSS_NST_SE-7.6 exam
Which statement about parallel path processing is correct (PPP)?
Refer to the exhibits.
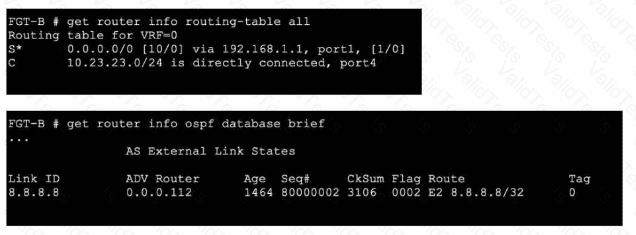
An administrator Is expecting to receive advertised route 8.8.8.8/32 from FGT-A. On FGT-B, they confirm that the route is being advertised and received, however, the route is not being injected into the routing table. What is the most likely cause of this issue?
Refer to the exhibit, which shows the output of get router info bgp summary.
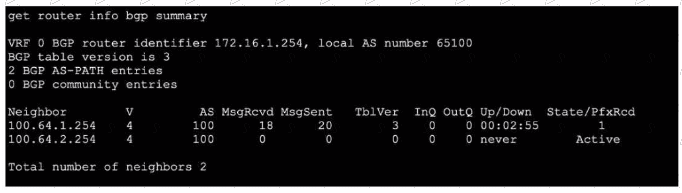
Which two statements are true? (Choose two.)
Refer to the exhibit, which a network topology and a partial routing table.
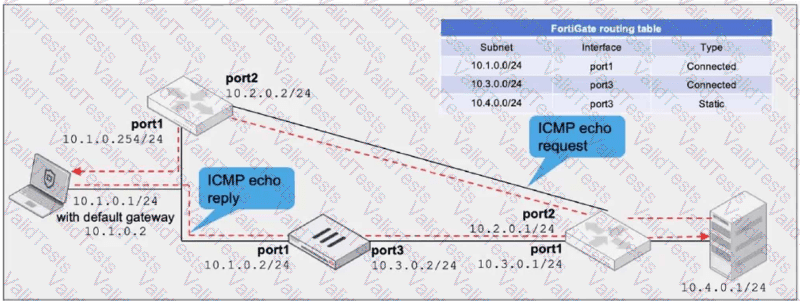
FortiGate has already been configured with a firewall policy that allows all ICMP traffic to flow from port1 to port3.
Which changes must the administrator perform to ensure the server at 10.4.0.1/24 receives the echo reply from the laptop at 10.1.0.1/24?
Refer to the exhibit, which shows a partial web filter profile configuration.
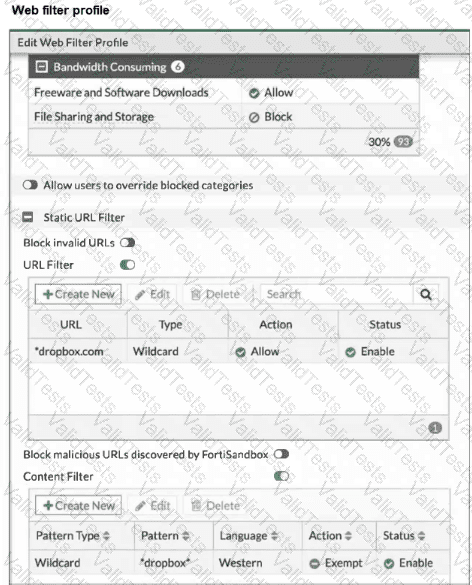
The URL www.dropbox.com is categorized as File Sharing and Storage.
Which action does FortiGate take if a user attempts to access www.dropbox.com?
Which authentication option can you not configure under config user radius on FortiOS?
Refer to the exhibit, which contains partial output from an IKE real-time debug.
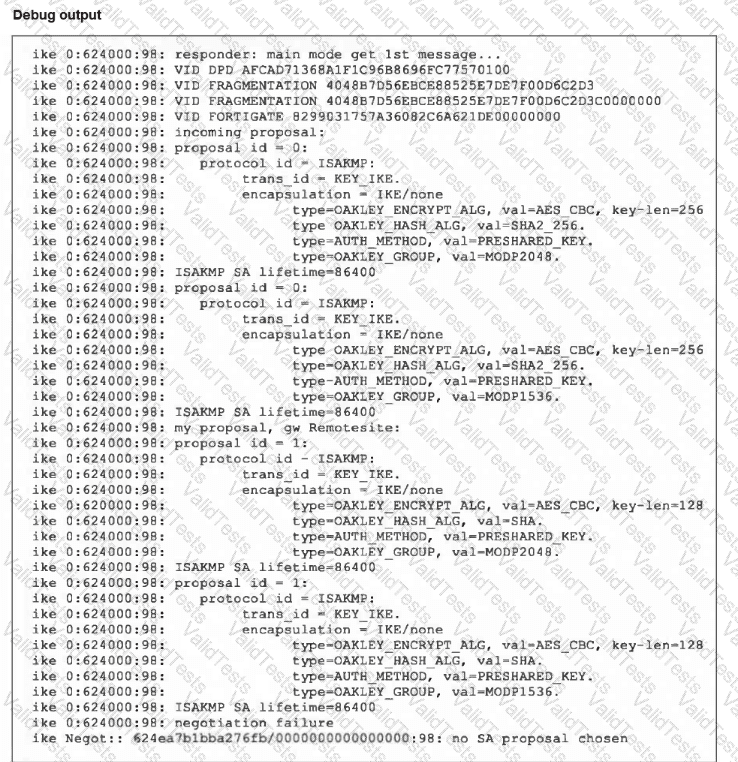
The administrator does not have access to the remote gateway.
Based on the debug output, which configuration change the administrator make to the local gateway to resolve the phase 1 negotiation error?
Refer to the exhibit, which shows one way communication of the downstream FortiGate with the upstream FortiGate within a Security Fabric.
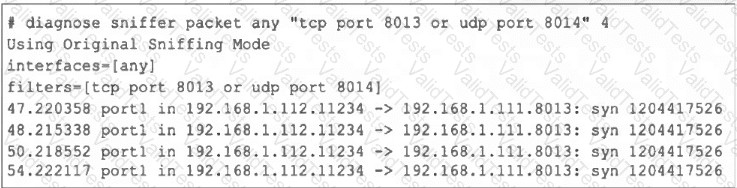
What three actions must you take to ensure successful communication? (Choose three.)
Exhibit.
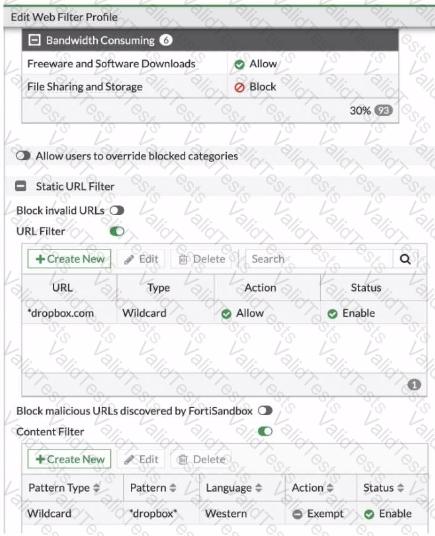
Refer to the exhibit, which shows a partial web fillet profile configuration.
Which action does FortiGate lake if a user attempts to access www. dropbox. com, which is categorized as File Sharing and Storage?
Refer to the exhibit, which shows the output of a debug command.
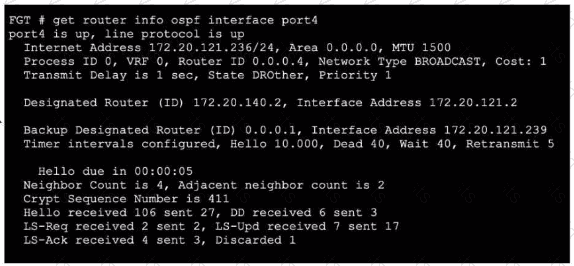
Which two statements about the output are true? (Choose two.)