Refer to the exhibit.
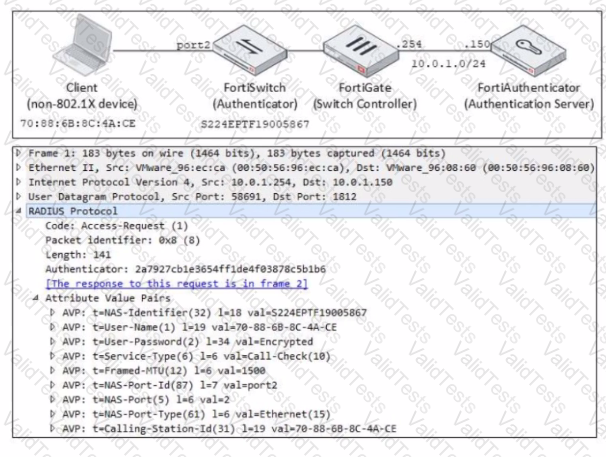
Examine the network diagram and packet capture shown in the exhibit
The packet capture was taken between FortiGate and FortiAuthenticator and shows a RADIUS Access-Request packet sent by FortiSwitch to FortiAuthenticator through FortiGate
Why does the User-Name attribute in the RADIUS Access-Request packet contain the client MAC address?
Which two statements about FortiSwitch trunks are true? (Choose two.)
Refer to the exhibits
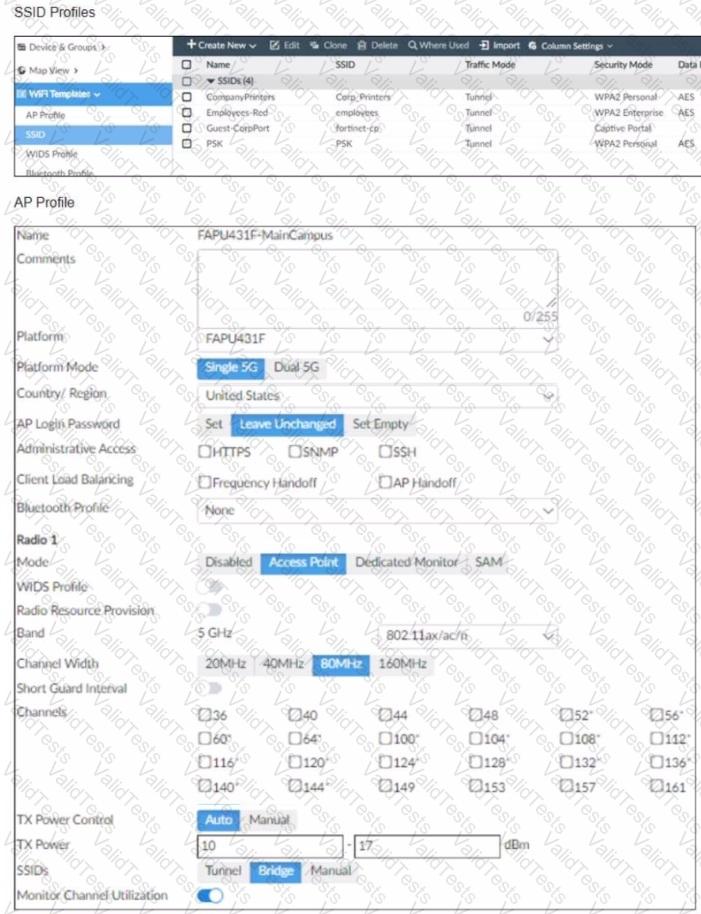
The exhibits show the wireless network (VAP) SSID profiles defined on FortiManager and an AP profile assigned to a group of APs that are supported by FortiGate
None of the APs are broadcasting the SSlDs defined by the AP profile
Which changes do you need to make to enable the SSIDs to broadcast?
What is the purpose of enabling Windows Active Directory Domain Authentication on FortiAuthenticator?
Exhibit.
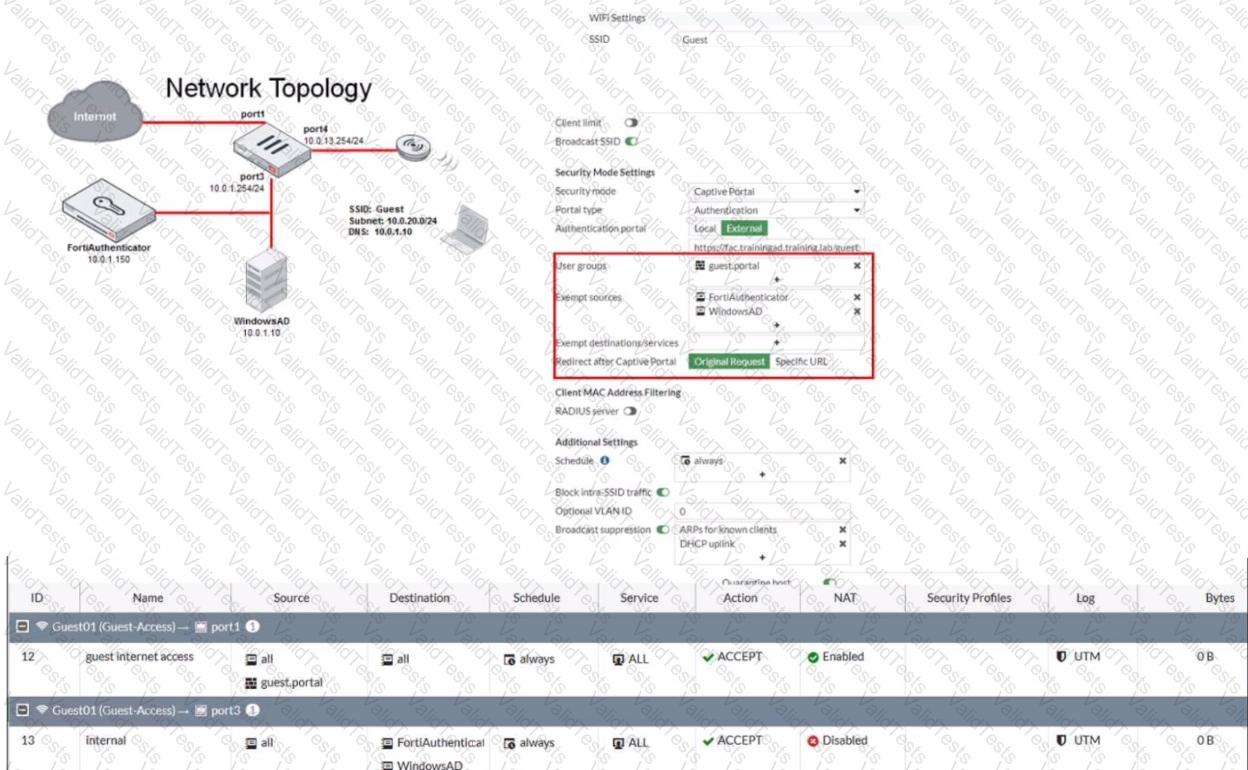
Refer to the exhibit showing a network topology and SSID settings.
FortiGate is configured to use an external captive portal However wireless users are not able to see the captive portal login page
Which configuration change should the administrator make to fix the problem?
Refer to the exhibit.

Examine the partial debug output shown in the exhibit.

Which two statements about the debug output are true? (Choose1 two.)
To troubleshoot configuration push issues on a managed FortiSwitch, which FortiGate process should an administrator enable debug for?
Which two statements about the use of digital certificates are true? (Choose two.)
Which three protocols are used for controlling FortiSwitch devices on FortiGate? (Choose three.)
Which two statements about the guest portal on FortiAuthenticator are true? (Choose two.)