
View all detail and faqs for the Deep-Security-Professional exam
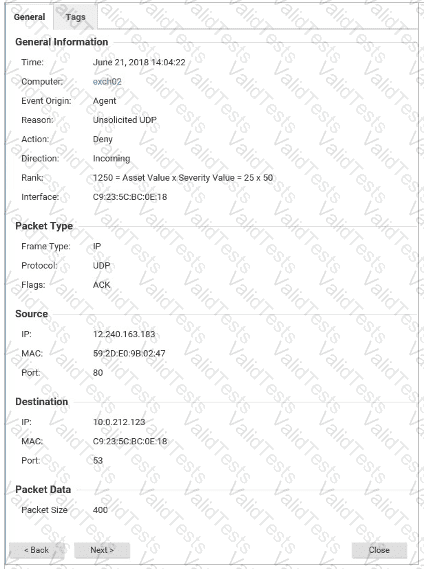
The details for an event are displayed in the exhibit. Based on these details, which Protection Module generated the event?
Which of the following statements is true regarding Intrusion Prevention rules?
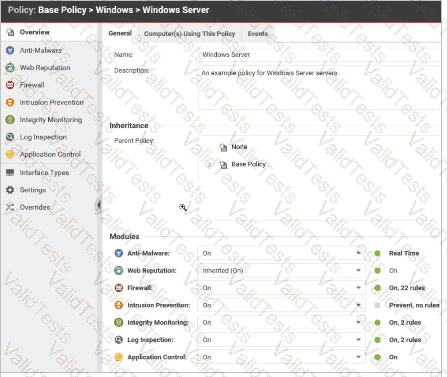
In the policy displayed in the exhibit, the state of the Web Reputation Protection Module is set to "Inherited (On)", while the state for the other Protection Module is set to "On". Why is the Web Reputation Protection Module displayed differently than the other Protection Modules.
Which of the following operations makes use of the Intrusion Prevention Protection Module?
How does Smart Scan vary from conventional pattern-based anti-malware scanning?
What is the result of performing a Reset operation on a Deep Security Agent?
Which of the following statements is true regarding the Intrusion Prevention Protection Module?
Where does Deep Security Manager store the credentials it uses to access the database?
Which of the following statements is true regarding Intrusion Prevention protection?
Which of the following statements correctly describes Smart Folders?