
Refer to the exhibit. An engineer must create a segmentation policy in Cisco Secure Workload to block HTTP traffic. The indicated configuration was applied; however, HTTP traffic is still allowed. What should be done to meet the requirement?
What does the Cisco Telemetry Broker provide for telemetry data?
A network administrator uses Cisco Umbrella to protect internal users from malicious content. A customer is using an IPsec tunnel to connect to an Umbrella Organization. The administrator was informed about a zero-day vulnerability that infects user machines and uploads sensitive data through the RDP port. The administrator must ensure that no users are connected to the internet using the RDP protocol. Which Umbrella configuration must the administrator apply?
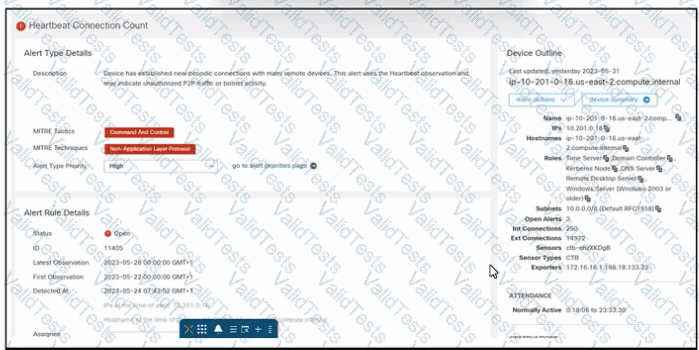
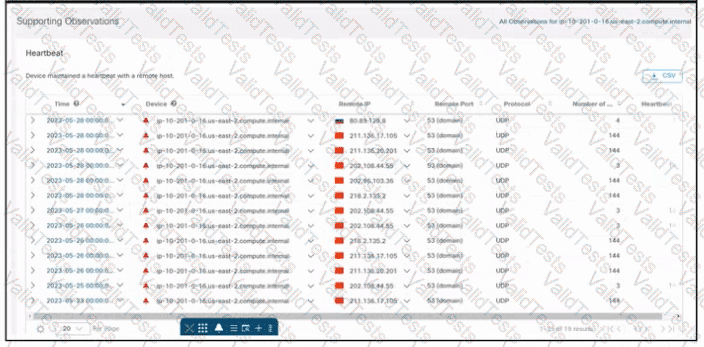
Refer to the exhibit. An engineer is investigating an unauthorized connection issue using Cisco Secure Cloud Analytics. Which two actions must be taken? (Choose two.)
An engineer configures trusted endpoints with Active Directory with Device Health to determine if an endpoint complies with the policy posture. After a week, an alert is received by one user, reporting problems accessing an application. When the engineer verifies the authentication report, this error is found:
"Endpoint is not trusted because Cisco Secure Endpoint check failed, Check user's endpoint in Cisco Secure Endpoint."
Which action must the engineer take to permit access to the application again?


Refer to the exhibit. An engineer must connect an on-premises network to the public cloud using Cisco Umbrella as a Cloud Access Security Broker. The indicated configuration was applied to router R1; however, connectivity to Umbrella fails with this error: %OPENDNS-3-DNS_RES_FAILURE. Which action must be taken on R1 to enable the connection?
What must be automated to enhance the efficiency of a security team response?

Refer to the exhibit. An engineer must configure Duo SSO for Cisco Webex and add the Webex application to the Duo Access Gateway. Which two actions must be taken in Duo? (Choose two.)
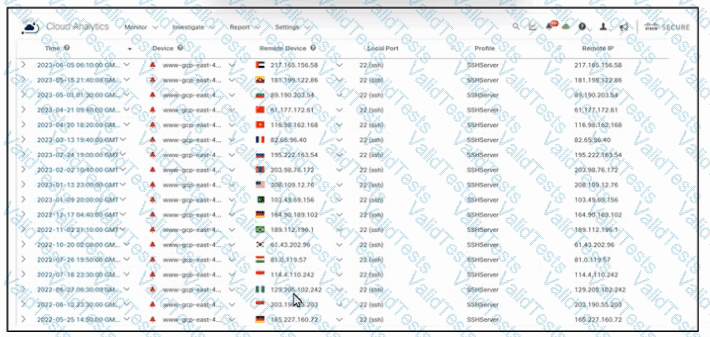
Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is occurring?
Which mitigation technique does a web application firewall use to protect a web server against DDoS attacks?