After gaining access to a previous system, a penetration tester runs an Nmap scan against a network with the following results:
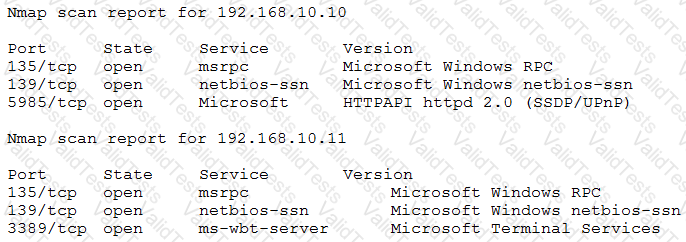
The tester then runs the following command from the previous exploited system, which fails:
Which of the following explains the reason why the command failed?
Submit